Category Archives: Government and Regulation
Sad declaration
“There have been zero successful cyber-attacks on critical national infrastructures in the past year”
This is what Yigal Unna, the head of the National Cyber Directorate of Israel, declared at the CyberTech conference, held last week in Israel. Stunning declaration in my opinion.
I thought there is no 100% in information security (which is true for physical security as well). How can he know this for sure? Information security, and certainly as part of risk management, involves recognizing that there is never any certainty. You can always be attacked successfully and you will know about it as it happens and you may never know. You always have to assume that at any given moment, at any part of your systems – you lose, because you know you don’t cover everything and can’t cover everything.
This is a statements in the style that existed before the Yom Kippur War. Smugness and arrogance that have no place in our profession and I believe that sooner or later they will run into the wall of reality and shatter.
How I found an open SSH access on an Israeli government’s gov.il DNS server
I have much criticism about the Israeli government information security status and activity. Lots of PR and marketing for being a “Cyber Nation” but it is true mostly for the selling of knowledge, services and products. Not so much doing the “dirty work” of protecting the Israeli Internet facing IT, including the one of the Israel government itself.
So, I started this weekend to operate a mini-project of checking the quality of HTTPS sites of the gov.il sub-domains. I publish the results in a public spreadsheet, accessible as read-only (viewing, downloading and printing is allowed anonymously) from Google – https://docs.google.com/spreadsheets/d/1Fez2A1FwqesWRuc2DowpdG20okh-KDbYfO5qnl8nZ-U/edit?usp=sharing
While running these checks I found something alarming:
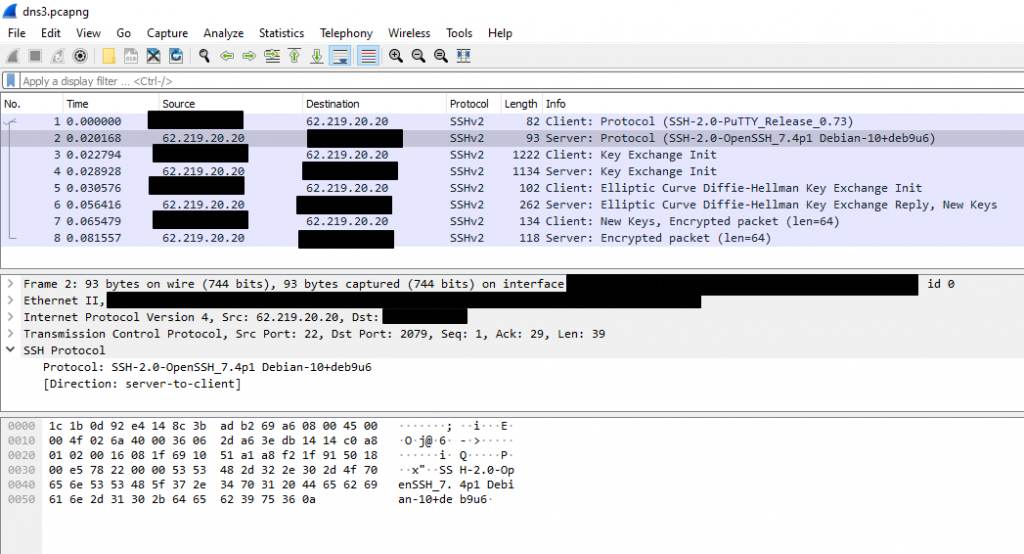
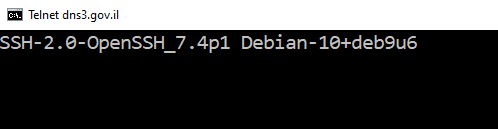
One of gov.il’s DNS servers, a server called dns3.gov.il, at 62.219.20.20 – replied at port 22 TCP, i.e. SSH, a service used to manage mostly Unix/Linux servers. Yes, open, allowing me try to login…
As I found it, in the afternoon of Friday, 31-Jan-20, I sent this finding at 16:28 to the Israeli national CERT and after ten minutes I also managed to correspond with someone I am in contact with, who was senior in government’s information security department, and he forwarded this issue to another security senior in the government’s IT, and he passed the details on to those who can fix this issue.
It took a few hours, but at the last check I did, around 21:30 that evening – access was blocked as this port has been closed, so it seemed to me that the issue had been addressed. Quite fast for almost Friday evening (the beginning of Shabbat in Israel).
Another point was that the SSH server identification was SSH-2.0-OpenSSH_7.4p1 Debian-10 + deb9u6, which means that the OpenSSH version is 7.4p1 that was released in December 2016, and since then several versions and a few security fixes for various security issues were released for OpenSSH, which are probably missing now from server. I hope they will update what is needed as soon as possible.
OpenSSH release notes
https://www.openssh.com/releasenotes.html
OpenSSH vulnerabilities
https://www.cvedetails.com/version-list/97/585/1/Openbsd-Openssh.html