Dig this – a bonus for you, my loyal readers… 🙂
Do not click on this link – https://2.21.143.74. It is the IP address of microsoft.com (the IP itself is of Akamai). Copy it to a clean Word document or clean Excel worksheet (make sure the apps are using the latest version of 365). Make sure the text becomes a link. Click on the link. A warning message will appear as in the attached image, stating that there is no match between the site you requested (because you requested an IP address) and the name of the site for which the certificate is intended (microsoft.com).
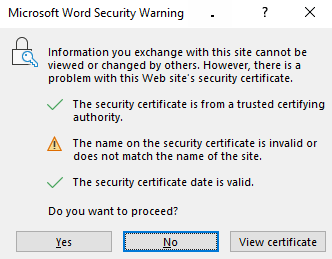
If you click “No” or the “X” button for closing the warning message window or even typing the keyboard combination of Alt+F4 to close the Word/Excel app – the link will open anyway … only killing the Winword.exe process for Word or Excel.exe for Excel – will cause the link not to open…
Also notice that the default focus in the warning window is on the “No” button, so a user’s automatic action (hitting “Enter” or “Space” on the keyboard or clicking the mouse main button, if the cursor feature of “Snap to default” is enabled) will cause the site to be opened instead of avoiding the site. That means that this protection does not work.
I contacted the MSRC with the above information, and they responded as follows:
“
Hello Eitan,
Thank you for submitting this issue to MSRC. We determined that while the issue you reported is valid, it does not meet our the bar for immediate servicing. That being said, this submission has been flagged for future review by the product team as an opportunity to improve the security of the affected product. We do not have a timeline for when this review will occur, and will not be able to provide status for this issue moving forward.
“